Imagine you work at Uber. You’re developing a new surge pricing model that will quintuple revenue and still barely make a profit. Life is good. You’re checking Slack before your next meeting, and you see a message in the #All-Uber channel that says:
“I announce I am a hacker and Uber has suffered a data breach. Slack has been stolen, confidential data with Confluence, stash and 2 monorepos from phabricator have also been stolen, along with secrets from sneakers. #uberunderpaisdrives”
You probably have questions… Is this a joke? What’s a phabricator? Why does this person not support the Oxford comma?
You’re about to Slack your team to ask if it’s real, but suddenly you’re locked out of Slack. What is going on!?
This attack happened in September 2022 at Uber (great write-up from the NYT here). While it’s rare to see hackers taking to Slack, it’s not rare to hear about hacks…
JPMorgan Chase had accounts hacked for 76 million households and 7 million small businesses in June 2014
Yahoo had data stolen from 3 BILLION accounts from 2013-2016.
Microsoft had its email exchange servers hacked for 30K companies in January 2021.
Facebook exposed user info and passwords for 530M people in April 2021.
In the last few years, there’s also – Marriott, Home Depot, Adobe, Ebay, Equifax, Target, CapitalOne, Zynga, and Cash App.
If you’re like me, the announcements about hacks start to become like white noise – always there, and easily ignored. What’s obvious from all these recent attacks, though, is that the attackers have the advantage and we need new defensive schemes.
Before we talk about those new approaches, let’s do a quick refresh on the history of cyber security.
A Brief History of Cyber Security

Physical security: The first computers were huge and not connected to the internet, so cyber security was just physical security. Restrict who can get to the computer, and you’re done. Easy.
Credentials: ‘Timesharing’ a single computer between multiple people was popular in the 1960s. At this stage, authenticating (proving who you are) became important, and you used a username and password to access your own files on the shared computer.
Firewalls: The US Dept of Defense innovated the internet into existence in the 1970s (I wrote about them spurring self-driving too…). Connections between computers meant an expanded “surface area of attack” for hackers to target. So network security, aka firewalls, exploded.
Antivirus: In the 1990s, viruses and malware took off, and that led to a surge in antivirus tools, malware scanners, and spam filters to try to keep bad actors out.
MFA: In response to data breaches and other hacks, MFA took off in the mid 2010’s (Obama even wrote an op-ed in 2016 for the WSJ declaring that passwords weren’t enough!). MFA combines factors related to: 1/ what you know (password), 2/ what you have (authentication app, RSA token, etc.) and 3/ what you are (biometrics).
But those haven’t been enough. As recently as a few weeks ago, there was another high-profile attack that feels like a Mr. Robot x Oceans 11 mashup.
Caesars Gets Hacked

A group of 20-somethings hit Vegas a few weeks ago, and it was wild. But not like the last time you hit Vegas, reader… they hacked it. The hackers, known as Scattered Spider, held Caesars’ casino systems hostage, and they got a ransom rumored to be $15-30M. MGM was hacked by a different group, ALPHV, and MGM claims that they have avoided paying a ransom. Instead, MGM opted to cut-off and rebuild the affected systems (which will still cost a boatload of money, just not paid to the hackers…).
As part of the response of the hack, MGM shut-off its casino networks (including TV and phone service), and casino staff were using pen and paper to track drink orders and cash-saddled managers to keep gamblers betting.
How did the hackers do it?
It’s hard to imagine anyone walking away from Vegas with millions more than what they arrived with, so it’s fascinating to hear about how they pulled this off (and instructive for how cyber security needs to evolve).
So here’s what they likely did (based on early reporting and write-ups of prior attacks):
Called IT – they called the IT helpdesk and impersonated an employee (using some details/info from LinkedIn). IT reset the credentials and provided them over the phone.
Sneakily used legitimate tools – By downloading tools that the company approves and some power users have access to, they avoided raising alarms while making their hacked user account more capable.
Flexed new muscles – With those new powers, they can push further into the casino’s networks, gaining access to data that becomes leverage when they install ransomware. The more data/access they get, the more painfully high the ransom.
We sometimes glorify bandits/cowboys in the US, but this level of access scares me a bit. So what are companies (and savvy individuals) doing about it?
State of the Art in Cyber Security
There are a few interesting angles of research into cyber security.
Zero trust – this is gaining popularity. It’s an approach that essentially locks down resources internally, so even if hackers get through a firewall or get into an individual account, they can’t move freely around. Imagine breaking into a bank vault and finding it empty, with 100 other bank vault doors now facing you. That’s the idea.
Passkeys – passkeys are designed to take the biggest vulnerability out of the equation – you. Rather than needing to provide/remember/reset credentials, passkeys use a biometric or a PIN on your device (ex. Apple FaceID).
AI-Assisted Monitoring – Hackers are using AI, so the good guys need to be using it too. AI can help identify suspicious patterns in usage. For example, if someone hacks your account and starts installing network administrator tools (but you’re a Sales Manager who has no business using those tools), it can flag and even restrict activity, even if you haven’t defined a specific rule for situations like that.
Security-centric approach – this approach tries to integrate and prioritize security, rather than making it a piecemealed, back-burner activity. Embedding security reviews into software development processes, prioritizing vendors that can offer more tools in a single/secure package, and building secure “mesh” to integrate your remaining security tools, are all ways to improve the security posture of a company.
And on a personal cyber security level, embracing friction (things that annoy you day to day) tends to be the right answer security wise. It’s annoying to have multi-factor authentication, but it’s extremely helpful. Even better if it uses an MFA app instead of sending you a text. Embracing passkeys and biometric keys (faceID, etc.) are all better than MFA. It’s also annoying to forget and reset passwords, but you shouldn’t have lists of passwords anywhere… no print-outs, no word docs, etc.
Things will get better, but until then… embrace the friction!
Bonus Bullets
Quote of the Week:
You can’t make money with a consensus accurate prediction.
— Bill Gurley, Legendary Venture Capitalist
Quick News Reactions:
Meta launched the Quest 3… It’ll be $500, or 1/6th the price of the Apple version… But on a side note, at some point they need to ditch “Quest” in favor of something that signals arrival. Until then I’m left wondering how confident they are!
ChatGPT hits the web…Paying users will have access to the internet-enabled version of the app. Honestly, this might make the results worse (more randomness and chaos on the internet, harder to predict where hallucinations might happen). I’m interested to see how users like it.
Apple is heating up… sorry, it actually looks like they are OVER-heating. Not good news for the latest iPhone model.
Tech Jobs Update:
Here are a few things I’m paying attention to this week:
Big Tech Job Posts: LinkedIn has 9,820 (+28.6% WoW) US-based jobs for a group of 20 large firms (the ones I typically write about — Google, Apple, Netflix, etc.). That’s the biggest jump and highest total I’ve seen since I started tracking last month.
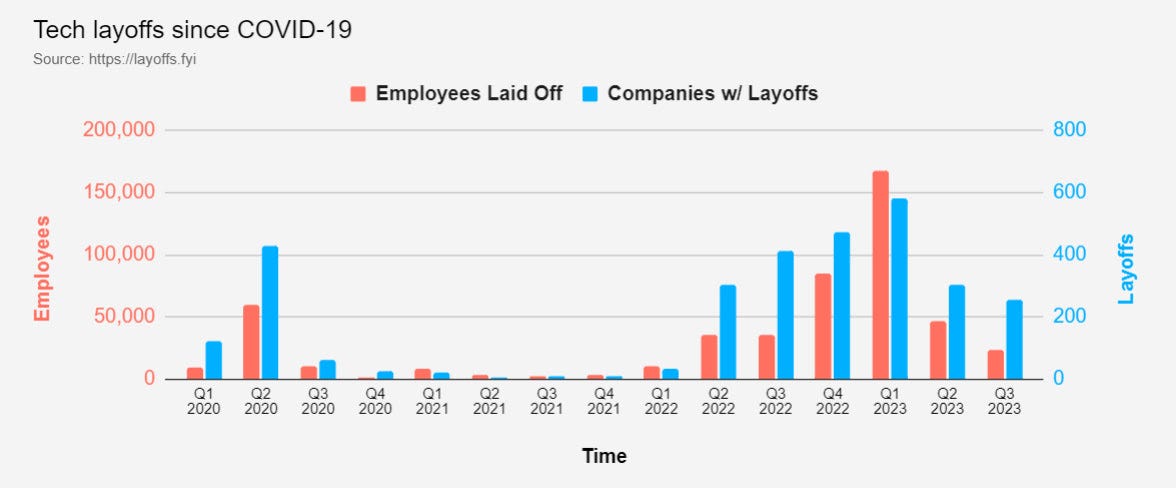
Graph: Layoffs since covid (Source: Layoffs.FYI)